To capture the business value from emerging technologies and reduce the chance of cyber attacks, manufacturers need to remain secure, vigilant and resilient.
If a cyber security breach occurs, are you prepared? With manufacturing facing such a dynamic cyber risk landscape, these seven steps are crucial to protecting your business.
1. Set the tone at the top
Employees need to be supported from the top to have a real impact.
Emphasising both the importance and consequences of cyber threats in the boardroom will ensure it’s respected and taken seriously company-wide.
The investments you’re making in emerging manufacturing technologies and connected products should all be covered by your cyber risk programme. But you don’t necessarily need to rely on your in-house team to drive this forward.
2. Perform a broad cyber risk assessment
Risks change and evolve over time, so performing regular reviews and cyber assessments can help identify potential areas of weakness in your IT estate.
3. Share the results
If the results of your cyber risk assessment are filed away, you’re missing a huge opportunity to create a visible, security-first culture within the business.
Share the results of the assessment and the strategy it has inspired. Encourage cyber awareness. Have discussions with each team about the impact of cyber risk on their work, and how preventative measures can help the organisation be more resilient to attacks.
4. Think data
Data is an asset. It’s essential to make sure you know where valuable data resides in your business, and how its risk profile changes as it makes its way through the organisation – from the supply chain, into business systems, the shop floor and out to third parties.
5. Consider third party risk
Working closely with third parties has the potential to expose your business to any cyber risks and vulnerabilities they have in their organisation.
Look at the critical relationships you have and how vulnerabilities in the ecosystem might have a knock-on impact to your risk profile.
6. Monitor constantly
To determine when and how a cyber breach could take place in key areas of the business, you’ll need to be vigilant in monitoring your IT estate. Cyber attackers exploit vulnerabilities, such as unpatched software and default passwords.
Implementing vulnerability scanning can reduce the opportunities for attackers to access your systems.
7. Get employees on board
The best cyber risk programme you could imagine is next to useless if it doesn’t gain buy in company-wide. Everyone has their part to play in a company’s cyber risk strategy, but do individuals and teams in your organisation know their responsibilities? Make it clear where the responsibilities lie for the crucial components of your cyber risk programme.
Drive awareness of your cyber strategies, and make people aware of their responsibilities. This approach mitigates phishing and social engineering risks, protects your IP and keeps sensitive data out of harm’s way.
Most importantly, ensure there are appropriate escalation processes in place that enable the reporting of unusual activity or areas of concern.
 Five boring but really important security mistakes you need to stop making
Five boring but really important security mistakes you need to stop making
Cyber security can be dull, but ignoring it won't make the problem go away. Turning a blind eye to your cyber defences leaves your business vulnerable to state-sponsored and ransomware attacks.
Download our free PDF guide to find out the top five critical security mistakes your manufacturing business is making, and what preventative measures can be put in place to solve them.
Find out more about how CORVID can benefit the manufacturing sector.
More CORVID blog posts
Cyber Incident Response for decision-makers
It is not unusual for an organisation to have a cybersecurity incident. It may be discovered through internal security controls (such as Anti-Virus, or a Security Operations Centre) , or it may be that a third-party notifies the organisation of an event.
When an organisation becomes aware of an incident it creates a chain of events that benefit from good decision-making. Most Boards are advised that they need to rehearse and prepare for a cyber incident. This can help. However, the majority of incidents do not need, or benefit from, Board-level oversight.
Whilst the decision-maker of an organisation is rarely a cyber-expert: they can play a critical role in achieving an optimum outcome. The following five-points are provided as a guide to the decision-maker.
1. Appoint the right leadership for the incident.
Incident response is a specialised field within the specialised subject of cybersecurity. The majority of people that work in IT or IT security (cybersecurity) have no experience overseeing a security incident. They may have a policy or strategy background and, whilst they may know the theory of how to respond to an incident, have very little hands-on experience.
The first decision that needs to be made is regarding the incident leadership. It may be that an in-house IT or InfoSec lead is exactly the right person to take-charge. If there is uncertainty that a suitable internal person can carry the responsibility the options are to bring in:
- a suitably experienced person to act as a mentor and guide to the in-house lead,
- an external specialist company to support the in-house lead,
- an external specialist company to take-over incident management.
It can be difficult for non-expert decision-makers to gauge whether an internal person is the suitable leader for the incident. Watch-out for the following warning signs that someone may be out of their depth:
- They are trying to apportion blame before the incident is remediated.
- They are using more jargon than usual and it’s hard to understand all the points they are making.
- Terms like “best practice” are used to justify an activity as opposed to an explanation.
The organisation must have confidence that the right expert is leading the response activity. But scared people rarely make the best-decisions. So even if the right person is on-point: they will probably benefit from some reassurance.
2. Set the communication tempo that is needed and try to stick to it.
Whilst it is tempting to want to know everything, every step of the way, this is rarely the most productive way of dealing with the matter. Minimising the communication burden can help maintain the focus on remediating the issue rather than communicating the issue. It is helpful to explain the tempo of communication updates or triggers that necessitate an additional briefing and then encourage the incident responders to get on with the job in-hand.
3. Agree the desired outcomes at the start.
Unfocussed incident response can quickly spiral into a mess. Set realistic outcomes such as:
- Contain the incident to as few hosts and users as possible: this helps recovery and reduces impact,
- Minimise downtime for the organisation and users: this helps maintain business as usual,
- Reduce the likelihood of this impacting other organisations: this helps protect reputation,
- Identify how the attack occurred: this helps prevent future incidents,
- Identify which files have been compromised (exfiltrated, changed, deleted): this helps comply with legal requirements of reporting and assess the longer-term business impact. This is critical.
Setting the priorities at the start helps direct the response. As more information is discovered the priorities may change. But when an incident takes on a life of its own it can be more damaging than necessary.
4. Forensic images are almost never necessary.
The main benefit of a forensic image is if there is a likelihood that there will be a court case at some point and evidence needs to be presented in such a way that it can withstand challenge.
The percentage of court-cases that result from a cybersecurity incident is very close to zero. The cost of capturing, recording and processing computers to a forensic-level is non-trivial. It will cause significant downtime, delay the determination of the impact to the organisation and potentially cost a lot of money.
If there is reasonable suspicion that the incident was triggered by an insider: then using computer forensics may be the right route to take. If this is the case consider the use of a specialist dedicated computer forensics team that are experienced at providing expert-witness.
Taking forensic images is no longer the standard approach taken for cyber incident response and it is rarely beneficial.
5. Make sure the response is less damaging than the incident
Rebuilds are often undertaken “to be safe”, even though the technical need for this is rare. This causes downtime and increases cost. If a rebuild takes place before the incident is analysed, it could result in critical evidence of attacker-activity being destroyed.
It is difficult to respond to a situation that is not understood unless an organisation is lucky. Relying on luck is rarely a good strategy.
There are cases of organisations switching off Internet connectivity, powering down server racks and shutting down critical systems. Whilst there may be a few catastrophic scenarios where this is the right thing to do: this is incredibly disruptive to an organisation and more often than not a panic-response. Make sure that the post incident assessment considers the disruption versus the risk to determine whether the response was reasonable and proportionate. Every incident is a learning opportunity.
Finally
There is no such thing as “perfect-defence”. Many organisations will deal with cybersecurity incidents at some point and the costs associated with data-breaches is reported as averaging millions of pounds. As an incident may involve PR and legal experts as well as the cyber incident specialists: costs can mount quickly. The decision-maker can play a key role in ensuring the right business outcomes are achieved.
An introduction to cybersecurity for decision-makers
Cybersecurity is an industry, a field of academia, a buzz-word, a science, an art and a bogeyman. And whilst cybersecurity cannot be avoided within any organisation that relies upon computers and data: there needs to be a way by which senior decision-makers can be involved in, and make decisions on, cybersecurity matters.
Cybersecurity is a highly specialised subject. It is complex and requires significant of knowledge and experience that is different from normal IT-knowledge. Knowing jargon and buzzwords does not mean that someone is an expert so always check the credentials of your “trusted advisors”.
Despite its overuse as a term, cybersecurity is fundamentally about protecting computer systems and data.
There are rules
Most territories now have laws around Data Privacy and many industries have regulations around information security. These must always be complied with and, irrespective of whether they are useful, they are necessary to operate in specific sectors.
Whilst the regulatory requirements may originate from the best of intentions: it is likely that organisations will need to do additional things to have the right type of cybersecurity for their specific profile and operations.
Why does anyone need cybersecurity?
Questioning why cybersecurity is needed is a good starting-point as it helps anchor solutions and initiatives to the fundamental driver behind activity in this space.
- The more you rely on (take advantage of) IT, therefore
- The bigger an impact to the organisation if something goes wrong, therefore
- The more you need cybersecurity
Cybersecurity needs to be seen as an enabler to using IT. Without cybersecurity, reliance upon IT is an incredibly risky thing to do. In-fact, one of the oldest risk equations in InfoSec (Information Security) works as follows:
Threat[1] x Impact[2] x Opportunity (Vulnerability)[3] = RISK
In mathematics if anything is multiplied by zero then the answer is zero. If there were no Threats there would be no Risk. If there was no Impact there would be no Risk and if there was no Opportunity to compromise a system there would be no Risk.
There are formal methodologies to measure the level of risk to an organisation as a result of a computer security breach. Sometimes formal assessments are useful to help shine a light on the scale of the issue. But if you are not required to undertake them then, in most cases, there is little benefit in going down this route.
Cybersecurity is a cost and, like other costs, it should be managed. For many organisations this means that the goal is to spend as little as possible on cybersecurity whilst having a proportionate level of protection considering the risk. Getting that proportionality right can be a challenge. Cybersecurity is routinely both a victim to underspending, where there is a lack of appreciation of the subject, and a cause of overspending, where the expenditure has not been objective focussed and consequently failed to achieve a useful outcome.
There are three fundamentals that an organisation needs to do regarding cybersecurity:
- Prevent an incident from occurring[4] – not all incidents can be prevented
- Detect an incident that has occurred – anti-virus cannot detect all incidents
- Respond well to an incident that has occurred – a good response can negate the impact of an incident
There may be exceptions to the above; but in-general all cybersecurity expenditure should be aligned to at least one of those three. Therefore, mapping initiatives against them can be a useful activity. Combining this with an articulation of effectiveness (a metric is best) is useful as it helps focus the initiative on the right outcomes for the organisation. At the risk of repetition: remember that cybersecurity is highly specialised. It requires specialist tools in the hands of specialist practitioners. Whilst an organisation could build their own Security Operations Centre (SOC), the question of “why?” should be raised. A company could generate its own electricity: but why would it do so?
Cyber expenditure almost always consists of both:
- Anticipated expenditure – the cost of the tool, service or technology
- Additional impact – specialist and (or) additional people, extra-training, recruitment, facilities and a distraction from core business
The following matrix (with a made-up example) is provided to help characterise cybersecurity initiatives. It is intended to be completed quickly, on the back of a post-it note, to help rapidly focus attention on the nature of the investment and whether the benefit, costs and approach have been considered. It is not intended to replace a full-investment case.
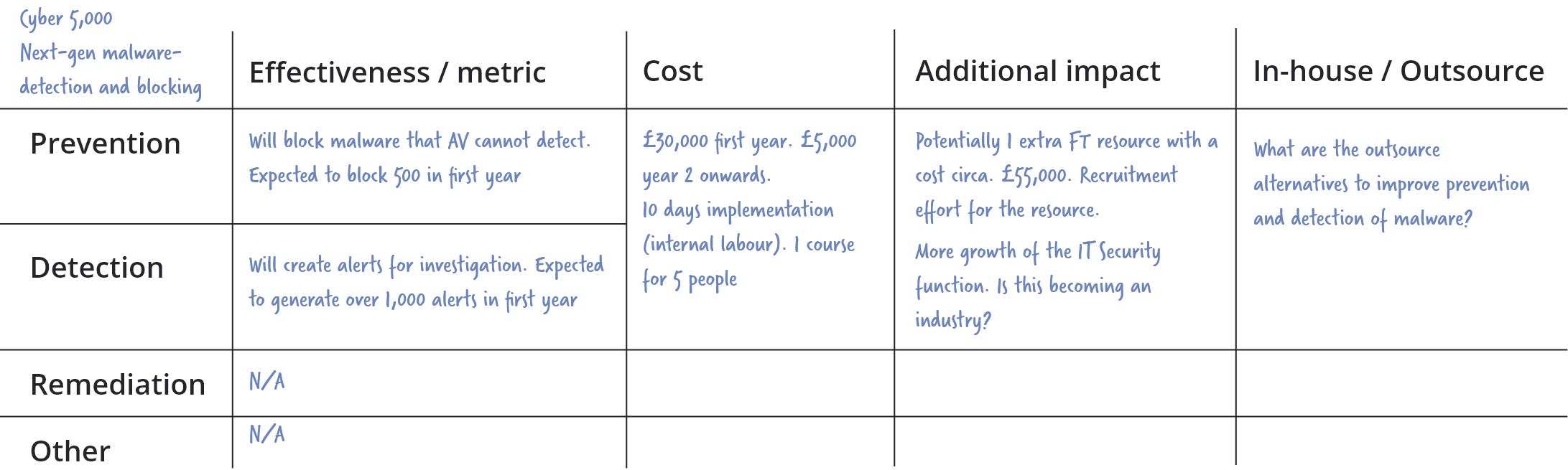
Final notes
No matter how much is spent on cybersecurity, and no matter what you are told, no company or product can guarantee safety. All anyone can do is make it less likely that an organisation will be compromised or reduce the impact of compromise. The inverse, i.e. not spending any money on cybersecurity, does not guarantee that an organisation will suffer a security breach. Not every organisation gets hit and some organisations are lucky. However, a strategy requiring luck is not recommended.
Whilst cybersecurity should be on the agenda: it should not monopolise it. Cybersecurity should be frictionless and, ideally, left to the professionals who should take the pain of it away. If cybersecurity is routinely causing you pain it is worth asking whether it is being managed as well as it could be.
Footnotes
[1] “Threat” refers to the groups or persons who do the attacking: Hackers, Nation States, Hacktivists. The entities that undertake the attack.
[2] Impact is not just the confidentiality breach of information. Depending on the circumstances, availability or integrity compromises can be highly impactful.
“Impact” is the impact to your organisation if they succeed in stealing, destroying, changing or making your systems and data unavailable.
[3] “Opportunity (Vulnerability)” is a measure of how accessible the systems and data are to attackers. Very secure government systems are not directly connected to the Internet and this reduces the Opportunity of attack considerably.
[4] Attackers have access to all the same technology that the defenders have and despite the prevalence of firewalls and anti-virus (both of which are much needed by the way), they are still able to breach organisations security and gain access to systems and data. Prevention is better than cure, but it’s just not practical to rely solely on this element.
Patching up life support: why critical care is at critical risk
Keeping people alive is unquestionably more important than patching software, but unpatched software is vulnerable to exploitation, and won’t keep anyone alive if it leads to a breach of your IT systems, rendering them unavailable.
After WannaCry exploited unpatched Windows XP vulnerabilities and cost the NHS £92m, healthcare providers across the country carried out a mass upgrade to Windows 10. Making the move to the newer OS is synonymous with increased security (you’d be worried if it wasn’t…), but there is growing concern that it was seen as a tick box, one-off exercise. Now the OS that was exploited is no longer in use, healthcare providers feel safer. This is a dangerously complacent assumption – new vulnerabilities are identified almost daily, creating an ‘arms race’ between attackers and vendors; one looking to exploit the other looking to get patches out.
The issue is further compounded as not all systems made it to Windows 10 – legacy IT systems remain where the service they provide can only run on the legacy OS. This particular stumbling block can make the health sector an easier target. Cyber attackers aren’t renowned for being a particularly moral bunch, so if they can shut down a hospital’s life support system and demand a hefty a ransom to get it back up and running again, they’ll take that payday without a second thought as to the consequences.
Let’s not forget that despite its wealth of valuable confidential data, the healthcare sector isn’t always necessarily the prime target for cyber criminals.
In the midst of the novel coronavirus pandemic, certain threat actor groups have claimed they won’t be targeting healthcare providers, but can’t rule out accidentally compromising systems if they’re not patched properly. Without a robust patch management programme in place, the sector can easily become an unintentional casualty of cyber attackers looking to exploit any vulnerabilities in any business. Just look at WannaCry.
The NHS is the nation’s beating heart, and healthcare providers know better than anyone that a beating heart stopping is a very bad thing. You can’t fix vulnerabilities you don’t know about, but you can guarantee threat actors will find them. You need full visibility of where your IT estate’s weaknesses are, and clear guidance on how to fix them. Even if you’re not a target, an unpatched infrastructure leaves you open to exploitation by opportunistic cyber attackers and widespread malware campaigns.
Most popular posts
1. Four questions you need to answer after a cyber attack
2. Three reasons the education sector is a prime target for cyber attacks
3. Law firms and cyber crime; the growing threat to the UK legal sector
4. Cyber Incident Response for decision-makers
5. How to effectively manage, detect and respond to a data breach





